|
Cyber security is the major concern for all the organizations in this present era. With the passage of every day, the cyber security risks seem to become more and more threat full. That’s why, every organization needs to have an adequate system which can save them from the drastic results. Talking about the big organizations, the security related matters for them are really sensitive ones. If somehow unfortunately they are attacked by a vulnerability, the recovery from loss for them is something like impossible. That’s why, a proper and adequate system for them become really crucial. How to remain Safe from Cyber Attacks? As we know that cyber-attacks are the major threats to businesses of the present era. It is really important to have an adequate system like managed SIEM. That’s the only way an organization can remain safe from the threats which have ruined numerous of well-settled ventures in no time. As an organization, it is important for you to understand what your status is when it comes to cybersecurity. You must be well prepared with an adequate and effective security system which can deny these attacks. Some Recent Surveys: There have been some recent surveys related to the security of different organizations from cyber attack, in which following results were obtained.
Some Really Alarming Stats:
Following are some of the really alarming and shocking facts that were revealed by the business executives.
0 Comments
Introduction: With the evolution and performance amplifications that are associated with technology, the need for makeshifts in hardware and security devices and approaches takes place and this is a normal practice. Shifting from one vendor to another or migrating may prove to be a challenging task. Many big names like in the security industry are always on their toes to get more clients however the actual efforts are made by their technical engineers who make things easy and possible when it comes to complex tasks like firewall migration. Why firewall replacement is considered critical? This is required to ensure smoother transitions, it is critical to ensure that all the seven OSI layers are performing well, i.e. from physical connectivity all the way through to application level. Following are eights steps for a success migration of firewall:
A good approach would be to look for reliable security solution providers who are rich in knowledge and can take good care of one’s need that fall within the brackets of firewall management. To be honest, being an active researcher in this domain, I have never come across a situation where I have met entrepreneurs who may have dealt with such situations in a professional way all alone on their own. Outsourcing is their ultimate way out and best bet. Dealing with security threats using free tools and approaches may not do the trick, besides it is not a lasting solution anyways when one looks at the constantly updating threat levels. With trends that are moving further into the elite zones that are backed with artificial intelligence and virtual reality and processes that are relying further on cloud technologies, smart and professional backups offered by third parties in this domain shall be considered by business owners with a serious and focused attitude. Wrapping up! We are operating in markets that are not favouring the idea of tampering with business processes, a better approach would be sticking to the basics. In today’s markets threats like security and cyber crimes are the key issues, dealing with them in a bookish and expert passion by working in a close collaboration with security solution providers will enable one to focus on business growth without any fear of data loss or unauthorised access.
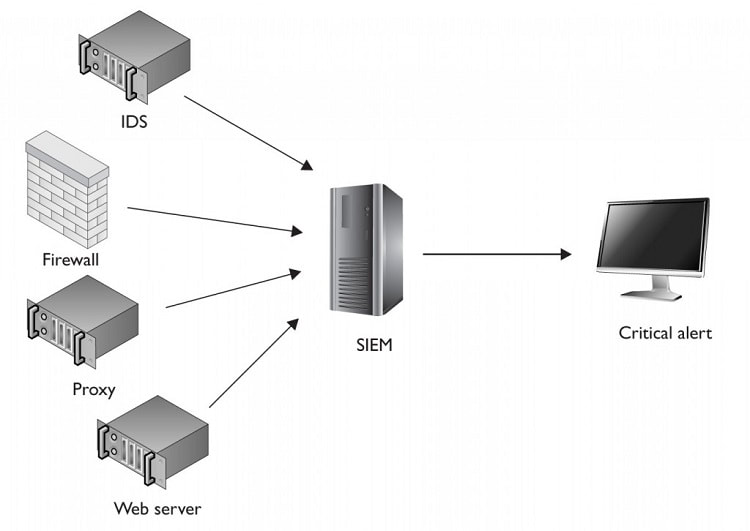
Introduction: It can be classified as a very reliable tool when it comes to safeguard companies irrespective of their size and operations. It helps in highlighting the weaker zones, detecting the threats and alerts the users for all the possible threats that may be faced by the company. This piece of writing is an attempt to provider reader with insights about SIEM software by offering a precise overview about it as a service. Definition of SIEM: It is software that is a blend of both security event management (SEM) and security information management (SIM). With the capacity of detecting threats, offering security alerts that are real time in nature and amplified complying nature, it really can perk up the security measures undertaken by a company. Talking about SEM only, it on its own focuses on the interpretation and data storage furthermore grabs information that needs to be analyzed and reported. After combining SIM and SEM the terminology SIEM makes it clearer for one to predict that both the systems are blended together so as to offer robust security solutions, analysis as well as detection of security threats while looking for them in real time. Some core benefits associated with SIEM as a service: Detection and handling of security threats in an efficient manner are among the many benefits that is associate with SIEM and this helps in making it an outstanding tool for organizations and their information technology oriented departments. Let’s have look at some additional crucial benefits that are associated with it:
Improved efficiency levels: Because of its collating nature, SIEM can gather data from various devices that are connected to the network; operators are enabled to utilize such information while detecting all the potential threats and issues with ease. Improved reporting, information gathering, scrutiny, analysis and retention With the help of efficient information security services, SIEM helps in reducing the influence of any security breach in a much reliable, swift and quicker passion. This helps in areas like reducing costs that may take place due to a security breach and at the same time helps in minimizing the damage that may have been caused to one’s business and its IT systems. A concluding note! There is a saying, ‘it is better to be safe than sorry’, can be applied here. Businesses, especially those that are involved in monitoring, storing and processing sensitive information of their clients and those that are connected with different interconnected network usually suffer when an unenthusiastic situation occurs. For lasting success and smoother transitions as far as business processes are concerned one must invest in security using a proactive approach. There is no point in panicking at the eleventh hour.
|
AuthorWrite something about yourself. No need to be fancy, just an overview. Archives
October 2018
Categories
All
|


 RSS Feed
RSS Feed
